The Importance Of Server Hardening
If you are working in any field, at least you have ever heard about the term “Server”. Especially in the IT field, you must know how vital servers are for the business because servers are places for businesses to store, access, and exchange data but they will also improve the efficiency and productivity of the business. Servers are a vital part of any company’s growth.
But, there are many servers on the world that were attacked every day, and the organizations are always looking for solutions to prevent those. So hardening a server is one of the right answers to protect your server your business. However, what is precisely server hardening? in this article, we will discuss and help you have an overview of server hardening and how important it is.
The term “hardening”
First of all, let’s define “hardening”. The term “hardening”, in the general, making a soft surface or material becomes stronger, hard to be broken and more resistant to damage. That is precisely how server hardening improving server security.

In other words “server hardening is the process of tuning the server operating system to increase security and help prevent unauthorized access”. Hence, hardening is to protect business data, intellectual property, and time from the hands of hackers by eliminating as many risks and threats to the system as necessary.
Why we need to harden a server
When we install operating systems and applications, they usually come with the default configuration/setting. Actually, the default configuration/setting of most operating systems and applications are not set to the highest security level. It concentrates more on usability that makes users feel comfortable and use the system easily.
Another thing, because it comes with the default configuration/setting, that’s mean hackers know what and how you had set up the servers, it will easily get cyberattack from hackers.
Those implied that if you don’t harden your system, your system will be running at a high level of security risk and that’s not good for the business at all.

So, the purpose of system hardening is to eliminate as many security risks as possible. This is typically done by removing all non-essential software programs and utilities from the computer. While these programs may offer useful features to the user, if they provide “back-door” access to the system, they must be removed during system hardening.
How do we harden it?
System hardening is the process of securing a system by reducing the vulnerability surface by providing various means of protection in a computer system. The protection provided to the system has a layered approach (see the picture below)
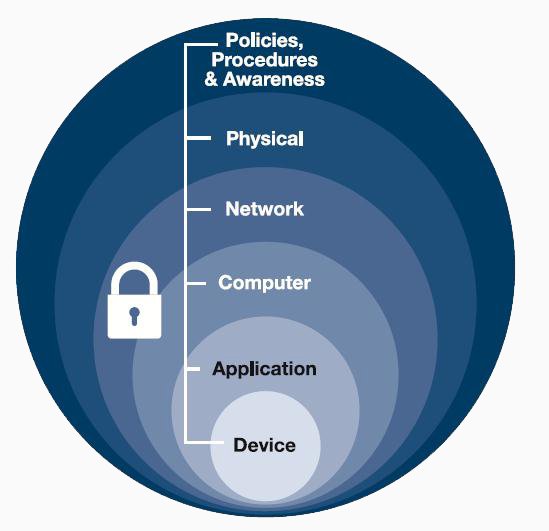
Protecting in layers means to protect at the host level, application level, operating system level, user-level, and the physical level. Method of security provided at each level has a different approach.
About the server hardening, the exact steps that you should take to harden a server will be different depending on the type of operating systems and applications you have. The list below is the typical checkpoint for the most popular servers for your reference:
- Base Operating System: All OS by default is not secure, it needs to be hardened for maximum security.
- Kernel parameters: Optimize kernel parameters to enhance server security.
- Shell Fork Bomb: Protect your server from users with terminal access who may inadvertently or intentionally cause a fork bomb.
- Remote Desktop, RDP: Tweak RDP settings to secure RDP access.
- Disable Anonymous FTP Access: Deny public from accessing FTP server with anonymous login.
- Secure PHP: Optimizing PHP configuration by restricting PHP, information leakage, disabling unnecessary modules/functions, tweaking PHP variables and installing Suhosin.
- System Integrity Monitor: The services will be monitored constantly for any failures and failed services will be automatically restarted.
- Firewall Fine-tuning: Firewalls are tweaked for increased security, resilience, and efficacy.
- Brute Force Detection: Detects unauthorized access to the server, and blocks attackers using sophisticated counter tools.
- MySQL: Better security by hardening MySQL server.
- Tmp directory security: Hackers usually try to upload unwanted programs or scripts in /tmp directory. It should be mounted on its own partition with limited permissions.
- Control panel Update: Always keep control panel software to the latest versions.
- Ngnix: Harden Ngnix settings for effective security lockdown.
- Mail Server Hardening: Tweak mail server settings to restrict incoming spam, spoofing, dictionary attack protection.
- Anti-Malware Configuration: Malware Scanner, effective for the detection of PHP backdoors, dark mailers, and other malicious files.
- Secure Shell SSH: Tweak SSH settings to secure SSH access.
- Apache: Most of the attacks happens on an insecure web server, harden it to max security.
- Compile Apache & PHP with updated patches: Apache and PHP scripts are subjected to vulnerabilities and should be patched periodically.
- DNS Attacks prevention: Avoid DNS amplification attacks from succeeding and using up your bandwidth.
- Mod_Security: Real-time web application firewall.
- Root Login Email alert: Alert server owners on root logins.

Additionally, the following server hardening checklist is a good place to start when hardening any types of the operating system:
- Firewall Configuration: Your server may or may not have a firewall set up by default. Even if it has one, these firewall rules may not be secure enough to protect your server. For this reason, you need to review the default configuration, just allow IP addresses and ports which are strictly necessary. Non-essential open ports may cause security risks.
- Access Control: As you know, all operating systems such as Windows, Linux, all provide user, group and account management features which can help us prevent unauthorized access to files, server or remote to the server. Review them and make sure that only give access to those who really need it. For example, in a Linux server, each user has read access to other users’ home directories, you would like to change file permission to remove unnecessary access.
- Software-update: In order to get the best performance from your server, most importantly, to prevent the server from being attacked, updates need to be addressed. In general, when updating software that’s mean bugs are fixed, especially, security vulnerabilities are patched. One software with a security hole open can cause terrible things to the software and the entire server system. And another thing, when you update software, you can get new features, changed style, and improved performance. Although it is not very important, it is nice to get one.
- Disable or remove unnecessary services and applications: Before doing this, you need to determine which services, applications can be disabled or removed. Sometimes, these services or applications could be one of the reasons causing security risks. There may be applications and services which aren’t supported or updated anymore. Hacker will attack the server through vulnerabilities on these apps and services. Your disk can get more space when removing these services and applications.
- Establish a password policy: Using a simple password that contains your birthday or username or your phone number. Make it easier to be cracked, so establish a password policy for all users is a good solution. In an operating system such as windows, Linux, they all have a place to configure password policy. That can help all users have strong passwords.
- Logging and Monitoring: Make sure that your logs and monitoring are configured and collecting the data you want when there is an error or an event happening, so you can quickly find what you need and solve the problem.
- Using encryption for sensitive data stored.
The things mentioned above are just actions that are usually taken when doing server hardening. However, you can get more best practices for securing server system from reliable organizations such as:
- Center for Internet Security (CIS): the CIS Benchmark provides practices for the secure configuration of almost every operating system, it is available for free.
- STIG Viewer: The Security Technical Implementation Guides, similar to the CIS Benchmark, it also provides guidelines for security configurations across multiple systems and is free as well.
- Microsoft: With windows server, you can get a security baseline which is a group of recommended configuration settings that explains security impact.
The benefits summary
- Reduce holes security: Hardening that’s mean server security is on another level. Vulnerabilities have been significantly decreased. Reducing attack surfaces and improving security.
- Save money in the long run: A hardened server has fewer security incidents, that’s mean you can save money in other areas of IT operations.
- Improve performance: As we said above, updating software, removing unnecessary services, applications can increase server performance.
In Conclusion
Hardening a server is an excellent solution to protect and probably one of the most important tasks to be handled on your server. Still, it is impossible to prevent cyberattacks completely. But spending enough time to harden server can help you avoid the attacks at the minimum cost and it will play a role as your final line of defense in case something goes wrong.