Client
The Land Information Management System (LIMS) project is an initiative of the General Department of Land Administration, funded by the World Bank Group. The LIMS project is expected to address all functions of the land sector, delivering tools for handling all land management functions, improving the security and reliability of land transactions through an efficient and reliable land information system.
The new system serves thousands of staff and ensures a smooth customer experience for millions of guests. The client needed a trusted security partner to identify vulnerabilities and provide guidance for remediation while meeting the compliance and regulation standards and protecting the user data.
Challenges
The new LIMS system allows the management of the land administration process to take place entirely in an internet environment. The land management functions and registration documents are submitted online. Due to the new process, many challenges that the project team and client were considered as below in order to assure that the system implementation can protect the privacy and confidentiality of users’ data as well as the security and availability of the whole system.
-
-
-
-
- Sensitive data like personally identifiable information (PII) exposure (Identity theft). The client has great concerns regarding user identities, it’s easy being targeted by hackers.
- Forgery of documents. Supporting documents such as proof of sufficient financial means, certificates of occupancy, customary rights, land administration dossiers … – are submitted in digital format, thus increasing the risk of documents being falsified.
- The system is open to the world, it must stand against all kinds of attacks: Spoofing, Denial of Service, Network congestion, Spam, Advertisements, Unauthorized Access, Sensitive Information Disclosure (SID), Spyware, Disabling applications or the device, Client-Side Injection/ Malware, Phishing…
- Keep server downtime to a minimum under attack.
-
-
-
Additionally, the time for penetration testing is rather limit and the testing is carried out parallel with development activity. But, the testing team has to perform the penetration testing on 2 major modules (one for public service, one for land management), and a lot of other functions, also has to ensure that the system can handle up to 10000 users using the system at the same time.
Solutions
Penetration testing can be conducted in many ways and methodologies. In this project, we apply the following methodologies:
-
-
-
-
- MeU Penetration Testing Standard
- OWASP Application Security Verification
- Information Systems Security Assessment Framework
- SANS: Network Penetration Testing and Ethical Hacking
-
-
-
And we followed this process in our project:

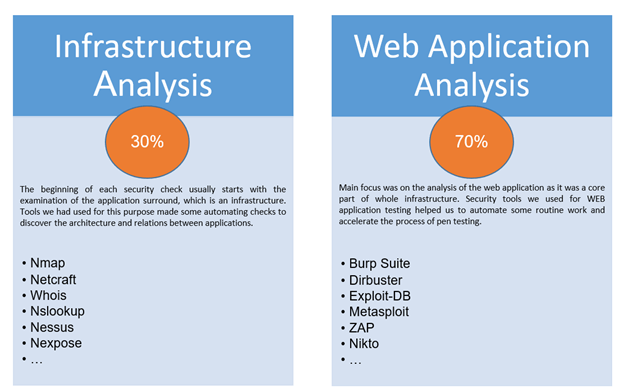
Used tools for pen tests in this project:
| For infrastructure tests, we divided into two categories: | For web application penetration testing process has three levels of testing: |
|
|
Results
With a team of 4 engineers and a duration of 3 months, we were able to fully compromise not only the organization’s infrastructure but also, web applications as well as expose critical data related to key organizational stakeholders.
Additionally, after this penetration testing was complete, MeU conducted training for the key internal security team as well as further advisory on remediation tactics. In the end, our client was able to meet the highest level of compliance and regulation standards, develop better security practices.
Below are some notes in our test report:


-
-
-
-
- 225 security bugs raised in categories of handling inputs, broken access control, bypass authentication, XSS,…
- The system was patched and configuration changes were made to mitigate the security risks.
- Successfully defined follow-up actions, mitigation plans and continuous procedures to minimize security risks
- The testing has achieved the goals that figure out weaknesses that exist and enhance the security system.
-
-
-





