A Story of MeU Approach’s Security Testing
In late days of December 2016, MeU Solutions obtained a contract for a 20M+ USD project from government. This project opened a new opportunity to grow our service expertise about security testing. This story is to tell about how we approached the security testing for that project.
Because of legal constraints, we are not allowed to expose much info about this project and all relevant services which are provided by the application. Therefore, we use the Project X as a replacement.
Cybersecurity testing is rather new to testers in Vietnam in general and MeU Solutions in particular. However, recognizing high needs from the markets as well as we believed that cybersecurity testing helps us to stay on the top of testing technology and quickly to be a leading testing technology vendor in VN. So, strategically we decided to invest to build this kind of service that started off with hiring and training talent QA Specialists.
Background and Introduction
The Project X is a big challenge, but it also is a great opportunity to bring our plan into the exercise. A team of four security testers was assigned in this project. The Project X is to provide a wide range of governmental services for 40 countries in the world. The system serves two user groups: (1). Individual who wants to sign up the services with a given fee. (2). Trusted organizations which are approved by the government, these organizations legally allow to register services for individuals.
The system is analyzed as a target of attack when it has impacts on political & national security aspects. In addition, the system focuses almost exclusively on the protection of personally identifiable information (PII) from a cyber threat perspective. We found that different adversaries will target or pursue the compromise of sensitive data records. With all these things, security becomes higher important than functional testing. The testing mission was limited at 6 weeks only
Gather Info and Establish the first stone
Our testing process designed to throughout 5 phases Security Scope Identification, Info Gathering, Threat Modeling, Vulnerability Analysis, Exploit & Perform the tests & Reporting. The Scope Identification and Info Gathering were the first two phases to establish first stones in our security testing. However, it was very difficult for us to meet key stakeholders who really understood the needs, were able to classify and to clarify sensitive data. To overcome these challenges, we decided to pairwise exploring with functional testing teams and tried to obtain as much as possible the application knowledge, prepared a list (in form of Mind-Map) of our know-how of application & services for rare meetings with key stakeholders.
Identifying different adversaries was a highlight of process for threat modelling correctly. Paying all attentions on just only unsophisticated adversaries was not enough to come up with a good threat model. As our analysis, three groups of adversaries must be included into the testing strategy including:
- Individual & Small Group
- Political Groups
- Organized Crime
Security level becomes low because the trust boundary is high
One of the meetings to gather information, our team sat with a key stakeholder who had total power to make all technical decisions and the application architecture. While the meeting taken smoothly, a point turned out a lot of concerns about security
As mentioned, one of user category is that trusted organizations which are given a token for sign-in the system with admin account (username and password are required). This token is generated by the government. With this mechanism, it is safe. However, this account is functioned to create other accounts (with only username and password required to sign in) which are able to register the service for individual. In their sense (key stakeholders), they certified and authorized these parties, so they trusted them. However, these organizations cannot protect themselves from attack. Unless appropriate security professionals exist within these organizations, it will be very difficult to secure that infrastructure or to understand the threats they face. Therefore, giving more permission, having more risk of security. To this issue, we recommended using 2-layer authentication to reduce the risk
Coming to the end of this meeting, we identified some areas and data groups need to be protected. It is grouped into:
- System and Network Configurations
- Payment Process Application
- Approval Certificate Application
With data groups
- Financial data
- Personal data
- Approval Certificate
Threat Modeling and Effective Weapons
Effective risk management requires an understanding of both the system to be defended and the adversaries that threaten it. Threat actors’ intentions and capabilities need to be modeled and applied against vulnerabilities. There is a numerous tool available for our security testing, however, each of these tools can be beneficial in some security facets when using them in the right context. The image below illustrates how we were modeling our testing against combination of tools
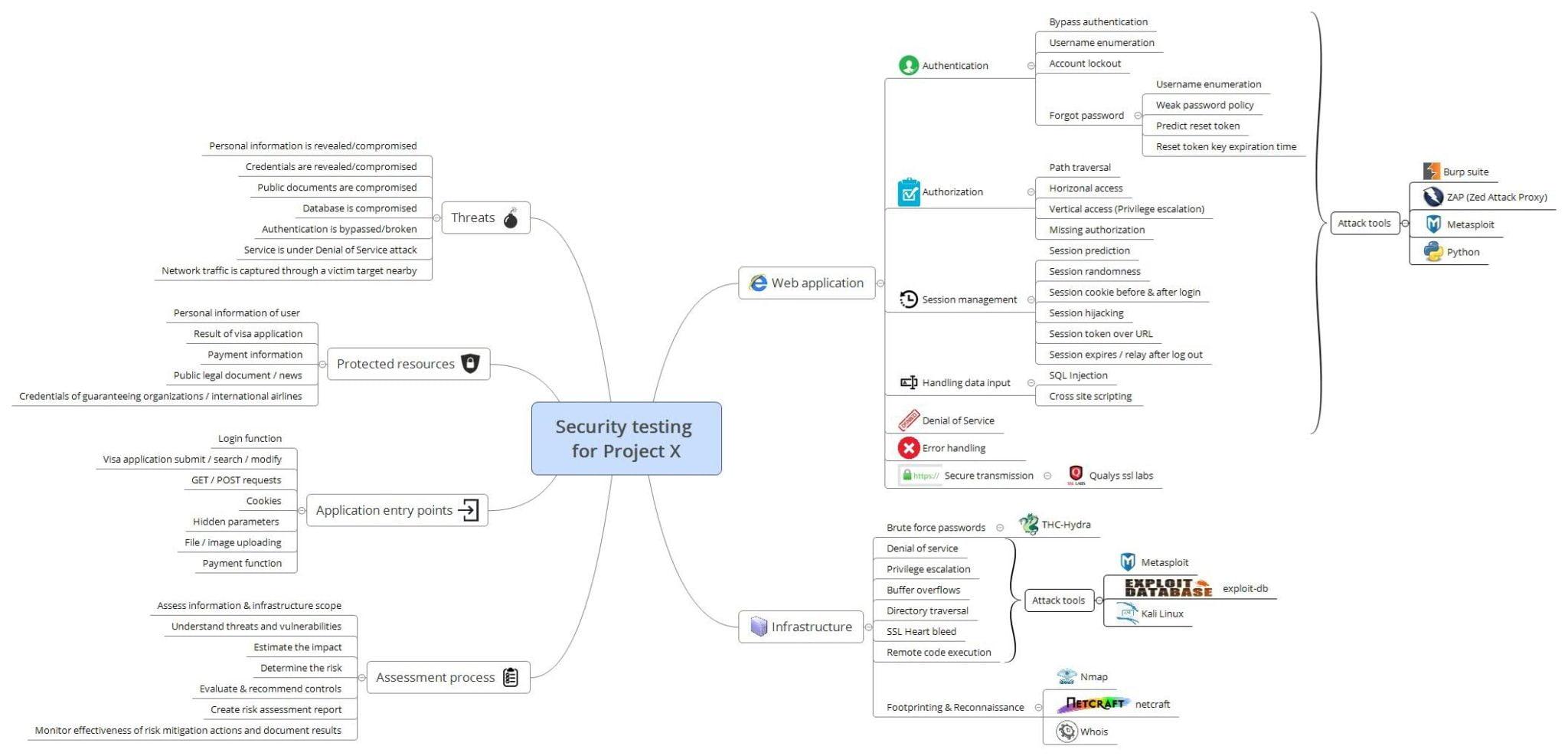
A set of vulnerabilities encountered such as: many ports being open; OS was not upgraded, Service application is obsoleted, brute force attack could be taken, private IP disclosure, cross domain source file inclusion as results from using right tools (weapons) in detecting vulnerabilities
The home is safe, but our neighbors are not
When almost unnecessary ports & services closed and shutdown; the OS and the Services has been upgraded, the opportunity to spot out vulnerability from system & infrastructure was closing. We intended to strive our effort into testing at application level. However, in last minutes of untargeted attack, we have recognized that the system with its IP being in a range of IPs from other machines (our neighbor) which have been serving other services for the government. As the result of our exploit, a bunch of ports being open from many other machines. In theory, we could attack or could attempt the access from these machines and waiting for opportunity (network sniffing or Trojan backdoor) to attack the system under test. However, the attack was not performed when we could not imagine what services being run on these machines. As a part of our mitigation, whenever a vulnerability was found, we disclosed all information to the client’s support team.
Your Application is simple, but the Attack is not
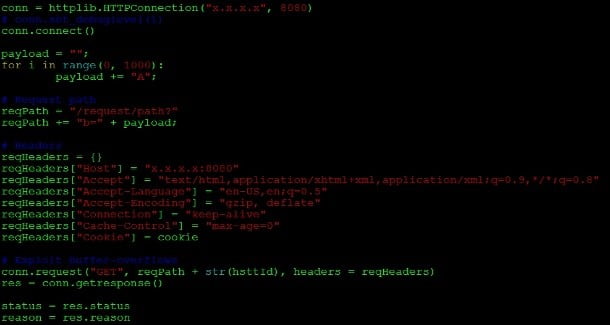
| Figure 1 – A piece of Python Code for Buffer Overflow |
The application is simple with its architecture. A simple UI to enter user profile. With these facts, we would need to check if sensitive data had to be encrypted during the transferring and all accesses to sensitive data had to be authenticated. By using SSL/TLS connection verification tools, constructing SQL injection/XSS/Buffer Overflow, constructing payload and launching the attacks, we could be rather confident at data protection. When everything almost done, one of our experienced engineer recognized that the application was accepting images/ pictures uploaded to the user’s profile. This is clue for other attacks. Immediately, he wrote a malware code to inject into the image. The code was to perform intended actions and attempted database access. This vulnerability was reported to dev team after the attack with fingerprint clue
Reporting time – Wrap up testing, but Security never ends
Many other methods taken within only about 2 months, 24 security bugs reported in category of Handling Inputs, Authorization, XSS, Data breach, Insecure direct object reference, Server Configurations, Firewall configurations. We were running out of the time and the system at that moment was low risk. It was a time to wrap up and report. However, we understand that the security needs still there. It is a process never ends. We need to make our stakeholders aware that security testing is the soul of their services. It is not one time investment.
Check out MeU Solutions Security Testing Solutions at here.

